While understanding Newton Protocol (NEWT) is important, applying that knowledge is where the real growth happens. Create Your Free Crypto Trading Account to practice with a free demo account and put your strategy to the test.
What Is Newton Protocol (NEWT)?
Newton Protocol is a decentralized infrastructure that creates a public compute layer and policy engine for verifiable automation. It empowers developers and enterprises to execute complex logic off-chain while maintaining full transparency and security on the blockchain. The protocol specifically focuses on enabling advanced functionalities not feasible with traditional smart contracts alone.
This technology directly solves the challenge of verifiable computation beyond the typical smart contract execution limits. It democratizes access to secure, trust-minimized automation for various applications. Newton Protocol’s design facilitates the seamless integration of off-chain data and computations into on-chain decision-making processes, bridging critical gaps in Web3 development.
What is Decentralized Compute Layer?
Newton Protocol establishes a network of independent nodes. These nodes collectively form a decentralized compute layer. This layer performs off-chain computations for on-chain verification, ensuring both efficiency and integrity.
The protocol functions permissionlessly, allowing any participant to operate a node and contribute to the network’s processing power. Node operators secure the network by staking NEWT tokens, operating on a Proof-of-Stake (PoS) consensus mechanism. This structure incentivizes honest behavior and penalizes malicious activities.
The Role of NEWT as a Policy Engine for AI and RWAs
Newton Protocol extends beyond simple computation, acting as a programmable policy engine for advanced applications. This engine enforces complex compliance rules and risk controls for AI agents and Real World Assets (RWAs). It manages conditions such as KYC verification, transaction limits, and whitelist filtering directly on-chain.
The protocol provides a secure framework for AI agents to interact with blockchain ecosystems autonomously. This ensures their operations adhere to predefined, auditable guidelines. For RWAs, Newton enables dynamic governance, allowing tokenized assets to respond to real-world events or regulatory changes with verifiable automation.
How Newton Protocol Works: The Technical Architecture
Newton Protocol operates through a sophisticated technical architecture that combines advanced cryptographic techniques and distributed computing. This design facilitates trust-minimized, verifiable execution of complex off-chain tasks. The core components ensure data privacy, computational integrity, and seamless integration with blockchain networks.
The architecture centers on a three-step flow: user signs an Intent, solvers execute the Intent, and a proof is generated. This process ensures all computations are both executed and cryptographically verified. It represents a significant advancement in decentralized computation capabilities.
Trusted Execution Environments (TEEs) in Newton
Trusted Execution Environments (TEEs) are a cornerstone of Newton Protocol’s security model. TEEs are secure areas within a processor that guarantee the code and data loaded inside are protected in terms of confidentiality and integrity. These environments isolate sensitive computations from the host operating system and other applications.
Newton nodes leverage TEEs (currently utilizing platforms like Phala) to execute off-chain logic privately and securely. This capability anchors the trust in computations performed outside the main blockchain. The TEE ensures that even node operators cannot tamper with the executed code or view sensitive data during processing.
Zero-Knowledge Proofs (ZK-Proofs) for Verifiability
Zero-Knowledge Proofs (ZK-Proofs) provide cryptographic assurance that computations are performed correctly without revealing the underlying input data. Newton Protocol integrates ZK-Proofs to verify the integrity of tasks executed within TEEs. This combination offers unparalleled security and privacy.
After a computation completes within a TEE, a ZK-Proof is generated, which is then submitted to the blockchain. This proof enables the smart contract to verify the computation’s correctness without exposing any sensitive information. ZK-Proofs enhance privacy while maintaining full auditable integrity.
Intent-Centric Architecture and Automation
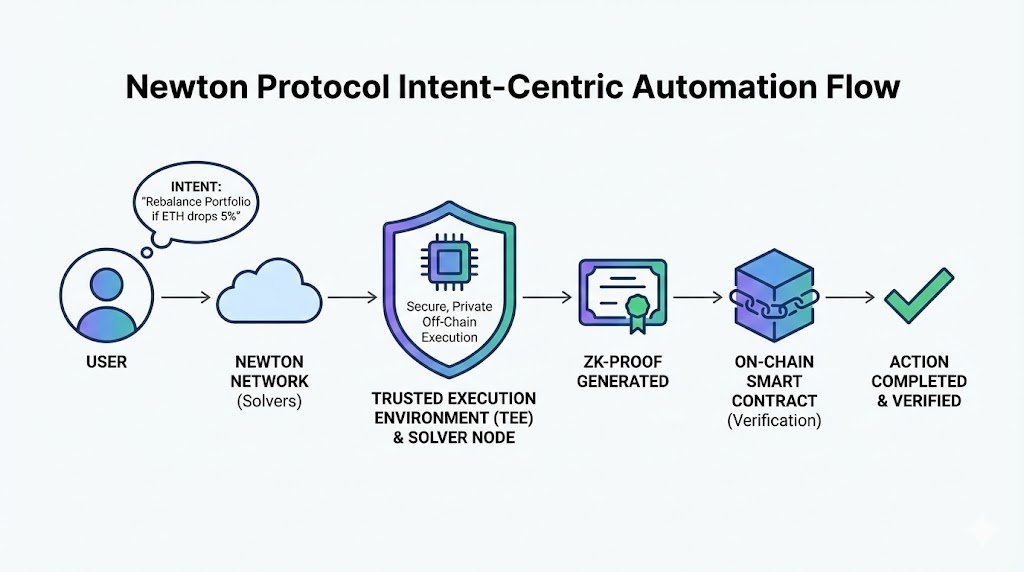
Newton Protocol employs an intent-centric architecture, simplifying complex interactions for users. Users express their desired outcomes as “intents” rather than specifying every step of a transaction. For example, a user might express an intent to “rebalance portfolio if ETH drops by 5%.”
The protocol’s network of solvers then competes to fulfill these intents. These solvers utilize their TEEs and ZK-Proofs to execute the necessary off-chain computations and on-chain transactions. This approach streamlines user experience and enables sophisticated automation, such as automated trading strategies or dynamic yield optimization.
Ready to Elevate Your Trading?
You have the information. Now, get the platform. Join thousands of successful traders who use Volity for its powerful tools, fast execution, and dedicated support.
Create Your Account in Under 3 MinutesCore Features and Utility of Newton Protocol
Newton Protocol provides a robust set of features that extend the capabilities of decentralized applications. It focuses on verifiable on-chain automation, enabling more complex and secure operations than previously possible. These features support diverse applications across finance, AI, and cross-chain environments.
The protocol’s utility stems from its ability to bridge the gap between off-chain computation and on-chain trust. This makes it an essential layer for the next generation of Web3 applications. It specifically enables advanced scenarios requiring privacy, complex logic, and external data integration.
Verifiable On-Chain Automation for DeFi
Newton Protocol enables verifiable on-chain automation for decentralized finance (DeFi). This includes automated trading strategies, liquidations, and complex risk management protocols. Standard smart contracts often struggle with the computational burden and data privacy requirements of these tasks.
Newton provides a secure environment for executing these computations off-chain. The system then submits a verifiable proof of execution back to the blockchain. This ensures that automated actions are both efficient and tamper-proof, reducing operational risks in DeFi applications. For example, an automated liquidation bot can trigger based on real-time price feeds, verifiable by the protocol.
Governance of Real World Assets (RWAs) and Stablecoins
The protocol serves as a critical infrastructure layer for the governance of Real World Assets (RWAs) and stablecoins. It provides a trust-minimized way to enforce compliance rules and risk controls on tokenized assets. This is vital for integrating traditional finance into Web3.
Newton’s policy engine manages various governance parameters for RWAs, such as interest rate adjustments, collateral management, and redemption mechanisms. For stablecoins, it provides verifiable proof of reserves and automated peg maintenance. This secure and auditable framework builds confidence in tokenized assets, a crucial step for mainstream adoption.
Cross-Chain Interoperability and Infrastructure
Newton Protocol supports cross-chain interoperability, allowing its verifiable automation services to extend across different blockchain networks. This is critical for a multi-chain future, as it enables seamless asset transfers and data sharing between disparate ecosystems. The protocol acts as a bridge, ensuring consistent policy enforcement regardless of the underlying chain.
The infrastructure provides a unified layer for managing complex operations that span multiple blockchains. This includes executing intents that trigger actions on Ethereum, then verifying outcomes on a different chain like Polygon or Arbitrum. Such capabilities enhance the utility and reach of decentralized applications significantly.
The NEWT Tokenomics and Ecosystem
The NEWT token is integral to the Newton Protocol ecosystem. It performs multiple functions that sustain network operations, incentivize participation, and govern future development. Understanding its utility and distribution is crucial for comprehending the protocol’s economic model and long-term viability.
The tokenomics model is designed to align incentives among node operators, developers, and users. This creates a self-sustaining and decentralized network. It ensures that the protocol remains robust, secure, and continuously evolving.
NEWT Token Utility (Governance, Staking, Compute Credits)
The NEWT token possesses 3 primary utilities within the Newton Protocol ecosystem. Firstly, it functions as a governance token, granting holders voting rights on critical protocol parameters and upgrades. This includes proposals related to fee structures or policy engine updates.
Secondly, NEWT is used for staking by node operators. Staking NEWT secures the network and ensures the honest execution of computations. Node operators earn staking rewards for their service, incentivizing consistent network participation.
Thirdly, NEWT serves as compute credits. Users pay in NEWT for executing intents and utilizing the verifiable automation services. This creates a direct demand for the token linked to protocol usage.
Understanding the Newton Airdrop and Distribution
The Newton Airdrop facilitates broad distribution of NEWT tokens to foster a decentralized community. Airdrop criteria typically include early testnet participation, providing liquidity to designated pools, or engaging with specific “Intent” functionalities on the platform. Eligibility for an airdrop might require holding specific cryptocurrencies or interacting with the protocol during a defined snapshot period.
For instance, the June 2024–2025 distribution cycle allocated 10% of the total supply to community rewards, with an additional 1.25% distributed via the Binance HODLer Airdrop for BNB stakers. Users who claimed and staked their tokens immediately were often eligible for additional bonuses, reinforcing long-term ecosystem health.
Market Context: Listings (Binance, Coinbase) and Price Volatility
The market context for NEWT includes its listing on major exchanges and its historical price volatility. Listing on prominent exchanges like Binance and Coinbase significantly increases the token’s liquidity and accessibility to a global investor base. These listings provide market validation and enhance trading volumes.
Following its mainnet launch in June 2025, NEWT reached an all-time high of approximately $0.82 before stabilizing as early airdrop recipients realized gains. As of December 2025, the token is actively traded across global markets, with its value closely tied to the protocol’s growing adoption among AI agents and RWA issuers.
Turn Knowledge into Profit
You've done the reading, now it's time to act. The best way to learn is by doing. Open a free, no-risk demo account and practice your strategy with virtual funds today.
Open a Free Demo AccountNewton Protocol vs. Standard Smart Contracts
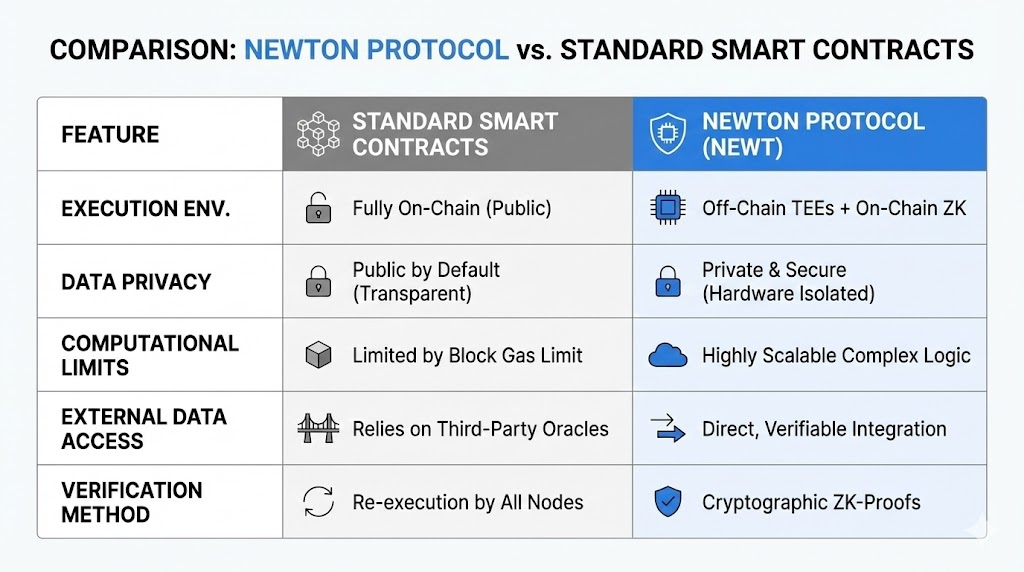
Newton Protocol significantly differs from standard smart contracts in functionality and capability, addressing inherent limitations of on-chain execution. Standard smart contracts are deterministic, transparent, and operate entirely on the blockchain. However, they face constraints regarding privacy, computational complexity, and access to off-chain data.
Newton Protocol overcomes these limitations by offloading complex computations to a decentralized network of TEEs. This enables private execution and verifiable integration of real-world data, expanding the scope of what decentralized applications can achieve. The core distinction lies in their execution environments and data handling mechanisms.
| Feature | Standard Smart Contracts | Newton Protocol (NEWT) |
| Execution | Fully on-chain | Off-chain (TEEs) + On-chain (ZK) |
| Complexity | Limited by gas / block size | Highly scalable complex logic |
| Privacy | Public data by default | Secure and private (hardware isolated) |
| Verification | Re-execution by all nodes | Cryptographic ZK-proofs |
| External Data | Relies on oracles | Direct verifiable integration |
Newton Protocol utilizes its compute layer to process off-chain data and logic. This allows for dynamic adjustments and complex rule enforcement that standard smart contracts cannot manage. For instance, a Newton-powered DeFi protocol can enforce sophisticated anti-money laundering (AML) checks using private external data, a task impossible for a typical smart contract.
The Future of Decentralized Infrastructure
Newton Protocol represents a crucial advancement in the evolution of decentralized infrastructure. Its unique combination of TEEs and ZK-Proofs establishes a new paradigm for trust-minimized computation and verifiable automation. This framework addresses the scalability and privacy challenges that hinder the widespread adoption of Web3 technologies.
The protocol’s role as a policy engine for AI and RWAs signals a convergence of emerging technologies. It provides the necessary plumbing for intelligent agents to operate autonomously and securely within decentralized networks. This also enables traditional assets to integrate seamlessly with blockchain ecosystems.
Newton Protocol anticipates a future where complex real-world conditions drive on-chain actions through verifiable, automated processes. It develops infrastructure supporting highly sophisticated DeFi products that respond dynamically to market events. It further establishes robust governance models for tokenized assets that comply with external regulations. The internet of value is becoming self-operating, secure, and private through the efforts of Magic Labs and the Magic Newton Foundation.
Key Takeaways
- Offloading is Key: Newton’s decentralized compute layer frees main blockchains from heavy tasks, boosting performance and efficiency.
- Hardware for Security: Trusted Execution Environments (TEEs) provide superior speed and crucial data isolation, making automation far more resistant to attacks.
- AI & RWA Protector: As a programmable policy engine, NEWT enforces complex compliance and risk rules for AI agents and tokenized real-world assets.
- Intent-Centric Design: Users define desired outcomes (Intents) rather than manual steps, allowing solvers to find the most efficient execution path.
- Verifiable Trust: Every action generates a ZK-Proof, ensuring that even off-chain operations are as secure and auditable as on-chain smart contracts.
Bottom Line
Newton Protocol is the foundational “automation layer” that Web3 has long needed to move beyond manual transactions. By solving the trust deficit in off-chain computation through hardware security and zero-knowledge proofs, NEWT turns complex intents into verifiable reality. Whether governing multi-billion dollar RWA portfolios or powering autonomous AI agents, Newton provides the secure, programmable policy engine required for the next decade of decentralized finance.






